

Our team consistents of four senior Computer Science students: Beth Hosek, Dena Schaeffer, Jacob Scheetz and
Justen Stall.
All of us being interested in the field of cybersecurity, we took a passion to developing a tool that could
actually make an impact on GE Aviation's Cyber Intelligence team. After all of the hard work
we have poured into this project to make it as practical, user friendly and effective as possible- we are
more than proud to present our fully functional Cyber Threat Intelligence command line tool, Cyber Turtle.
Get to know us, the Cyber Turtle development team, below:




Senior Staff Cybersecurity Researcher
GE Aviation
Cincinnati, OH

Assistant Professor, Department of Computer Science
University of Dayton
Dayton, OH
The goal is to develop a classification system that can analyze the text of a threat intelligence report and produce a score which quantifies the relevancy of that report to the receiving organization based on a list of user-defined relevant topics.
Our team has been working on the devlopment of a fully functional command line tool for GE Aviation, similar to those that are commonly packaged with security distrobutions of Linux. GE's Cyber Intelligence team faced a problem where their Intelligence Analysts simply did not have enough time to read all of their threat reports dilligently enough. That is where our tool, Cyber Turtle, alleviates the issue. Our tool has the capabilty to parse through some of the most common cyber threat report document types and then provide an analyst with a relevance score on each document based on a database of keywords given to us by GE. This provides the analyst to quickly parse an uncomprehensible amount of content and determine whether it's worth looking over to help secure the business.
This project will be used by GE Aviation's Cyber Intelligence team to provide a priority to their research of open-source intelligence (OSINT) reports.
As a global company doing high-value work, the volume of relevant reports published daily is too much for even a large team of analysts to read and understand quickly.
Our tool would help give priority to what reports need to be read first and what can be overlooked, making sure each piece of vital information gets the attention it needs to continuously give GE's Threat Hunting team a grasp on the cyber space that faces them.
Figure 3.0 - Live demonstration of how to use Cyber Turtle to view execution options
Figure 3.1 - Live demonstration of Cyber Turtle parsing an entire directory from a bash terminal
By enabling the verbose option, the user gets a live insight into:
Figure 3.2 - Live demonstration of Cyber Turtle parsing an entire directory from a bash terminal in verbose mode
Figure 3.3 - Live demonstration of Cyber Turtle parsing a single URL and providing a relevance score
Figure 3.4 - Live demonstration of Cyber Turtle parsing an RSS feed (collection of URL's)
Figure 3.5 - Live demonstration of Cyber Turtle parsing an OPML feed (file containing links to many RSS feeds)
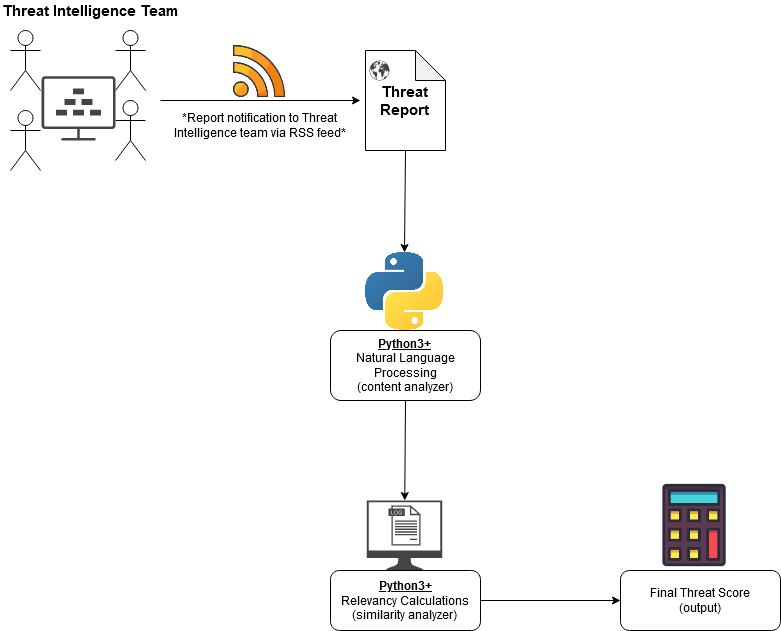
Figure 1. - A Sample of Overview Architecture of the project.
Figure 2. - A full system diagram of the project.